Ransomware poses a threat to you and your system, but what makes this malware so special? The word “ransom” itself tells you everything you need to know about this nuisance. Ransomware is software that encrypts the victim’s data and important files and then demands payment to decrypt the data.
Ransomware infection occurs as follows. The malware first acquires access to the device. Based on the type of ransomware, either individual files or the entire operating system are encrypted. A ransom is then demanded from the victim to decrypt the data. To minimize the risk of a ransomware attack, one should always rely on high-quality ransomware protection software.
These attacks take benefit of human, network, system, and software vulnerabilities to infect the victim’s device—which can be a computer, smartphone, printer, wearable, point-of-sale (POS) terminal, or other endpoints.
HOW DOES RANSOMWARE WORK?
The ransomware attack proceeds as follows.

- Infection—Ransomware is stealthily downloaded and installed on the system.
- Execution—The ransomware scans each and every network-accessible file, including local files, and mapped and unmapped networks. Few ransomware attacks also encrypt or delete any backup files and folders.
- Encryption—Ransomware executes a critical exchange with the Command and Control Server, using the encryption key to shuffle all files discovered during the Execution step. It blocks access to the data.
- User Notification—Ransomware adds a file with instructions describing how to pay for decryption and then uses these files to display a ransom note.
- Cleanup—Ransomware terminates and deletes itself, leaving behind only the payment instruction files.
- Payment—The victim clicks a link, given in the payment instructions file, which takes the victim to a web page with further information on how to make the demanded ransom payment. Hidden TOR services are often used to encapsulate and confuse these communications to avoid detection by network traffic monitoring.
- Decryption—Even when the ransom is paid by the victim via the attacker’s Bitcoin address, the victim may get the decryption key. But, there is no assurance the decryption key will be delivered as promised.

RANSOMWARE PROTECTION
Several best practices that can help you protect and prevent Ransomware infections:
- Endpoint Protection – Current endpoint protection platforms provide next-generation antivirus which protects against mysterious or confused ransomware like file-less attacks like zero-day malware or WannaCry whose signature is not yet found in malware databases. They also provide device firewalls and Endpoint Detection and Response, which help security teams detect and block attacks in real time.
- Patch Management – Keep the operating system, and installed applications up-to-date, and install security patches. Execute vulnerability scans to identify vulnerabilities and fix them quickly.
- Data Backup – Regularly back up data to an external hard drive/Pendrive. Disconnect the hard drive/Pendrive from the device to prevent encryption of the backed-up data.
- Email Protection – Educate employees to identify social engineering emails, and test if employees can identify and avoid phishing. Use endpoint protection and spam protection technology to block suspicious emails and malicious links if the user does end up clicking on them.
- Application Whitelisting and Control – Install device controls that allow you to restrict applications installed on the device to a centrally-controlled whitelist. Increase browser security settings by disabling vulnerable browser plugins and use web filtering to control users from visiting malicious sites. Disable macros on Word and other vulnerable applications.
- Network Defenses – Use a web application firewall (WAF), Intrusion Prevention, or Intrusion Detection Systems to prevent ransomware from communicating with Command & Control centers.
Recommended: http://techopedia.in/what-is-cyber-security-the-ultimate-guide-to-cyber-security/
RANSOMWARE DETECTION
- Real-time blocking is used to detect ransomware-specific read/write behavior and prevent users and endpoints from accessing further data.
- Use deception-based detection, which strategically implants hidden files on storage systems to identify ransomware encryption at the earliest attack stage. Any write/rename actions on the hidden files automatically block the infected user or endpoint, while continuing to allow access by uninfected users and devices.
- Use granular analysis and reporting to provide an unambiguous audit trail for forensic investigations into who, what, when, where, and how users access files.
- Deception-based detection measure guarantees that only the infected user is blocked from accessing data.
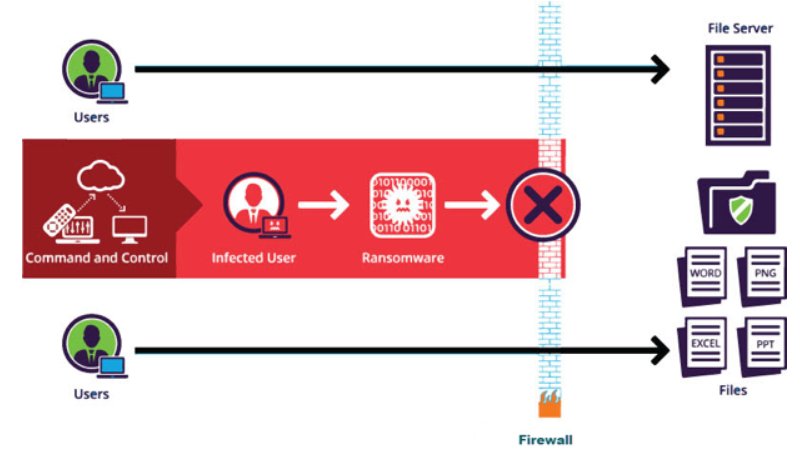
HOW TO MITIGATE RANSOMWARE
Here are the few immediate steps one should take to mitigate the ransomware threat:
- Isolate – Identify infected devices, disconnect from networks, and lock shared drives to control encryption.
- Investigate – Check the available backups for encrypted data. Identify the ransomware strain you are hit with, and if there are any decryptors available.
- Recover – Restore your data from backed-up devices, if no decryptor tools are available. Authorities do not typically recommend paying the ransom, but in extreme cases, it may be your only option. Remove ransomware by following standard techniques or wiping and reimaging systems affected by ransomware.
- Reinforce – Understand how internal systems were infected and how ways to prevent a recurrence. Recognize the vulnerabilities or security patterns that allowed the attackers in, and remediate them.
- Evaluation – It is imperative to evaluate what happened and the lessons learned. How was ransomware executed? Why did antivirus or email filtering fail? Which vulnerabilities made penetration possible? Was it possible to wipe and reinstall infected devices, and were you able to restore data from the backup? Address the weak points in your security posture to be prepared for future attacks.
Recommended: https://www.kaspersky.com/resource-center/threats/ransomware
CONCLUSION
Ransomware poses a significant threat both to private users and companies. This makes it all the more significant to keep an eye on its threat. And to be prepared for all eventualities. Therefore, it is essential to learn about ransomware, be aware of how you use devices, and install the best security software.
Even with the best security practices, a ransomware attack can never be ruled out completely. If the worst comes to the worst, excellent Internet security software and careful action can help to mitigate the consequences of a ransomware attack. The warning signs of a ransomware attack can help you to detect and fight infection early. Even if a ransom has been demanded, you have various alternatives and can choose the right one depending on the situation. Remember that backing up data regularly will significantly reduce the impact of an attack.